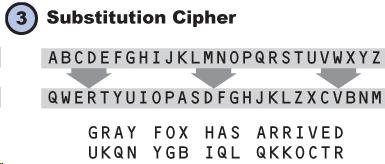
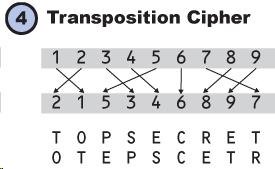
Security Threats
Problems like computers’ malfunctioning, unauthorized accessing, viruses inserting, DDOS attack will threaten the network security. I recommend you to watch this video youtu.be/AuYNXgO_f3Y which explains three types of threats: virus, DDOS, and phishing scam. Virus is installed in one device and can be spread spread quickly to other computers. Virus is used for stealing files in a device, causing malfunction, or enabling hacker to remotely control the device. DDOS (Distributed Denial of Service) occurs when millions, or even billion devices sending accessing requests to a computer causing the computer to stop responding. Phishing scam usually appears on some websites. Careless visitors may leak personal information like passports unconsciously. Then the visitors’ money got stole, for instance. To prevent network security, we use a technique called encryption.
Encryption
By using encryption, a computer encode a message into a form that can not be understood by an unauthorized person. The creation of this classified form involves couple mathematics algorithm. Only the person with correct key can decode and read the message. We called the correct key-Encrption Key.
There are two types of encryption: Symmetric-key Encryption and Asymmetric-key Encryption (AKA Public-key Encryption). Symmetric-key Encryption users use one key to encode and decode.
Symmetric-key Encryption
The Asymmetric-key Encryption users use public key to encode and private key to decode. This two keys are mathematically linked. Let’s imagine a condition, B requests to send a file to A. Then A sends its public key to B. And then B use A’s public key to encrypt the file and send it to A. Only A can use A’s private key to open that file.
Asymmetric-key Encryption
(Introduction To Cryptography)
The following two pictures show examples of how encryption and decryption work.
(Introduction To Cryptography)
Https & SSL
Https is a more secure version of Http. The “s” stands for “secure” and the security is provided by SSL encryption. SSL (Security Socket Layer) make a secure connection between the browser in your computer with websites’ servers. The browser communicate with the server using a language that only the browser and server understand. Then any third party will not be able to snoop any information that you have encrypted and understand your traffic. For example, Gmail is always https.
TLS and SSL are different versions of a same protocol. In this case of TLS, the browser and the server initiate a Hand shake procedure, and the server send back a certificate in a digital form to the browser. The certificate contains the server’s name, certificate authority, and the public key. Only when the certificate is reliable and updated, your browser will connect to the website server.
Ensure Network Security
There are three ways to ensure the authenticity when someone is trying access to your information.You should combine the following three factors to ensure the highest authenticity.
- Something you know (passport)
- Something you have (phone)
- Something you are (fingerprint)
There are many other ways to ensure the network security. For instance, you can choose to use multiple strong passports, or you can establish software, hardware, and router firewall.
MAC Address
We can block users by MAC address (Media Access Control address: A unique address on each device used to identify each user’s connection to the media, for example, the connection to the WiFi)
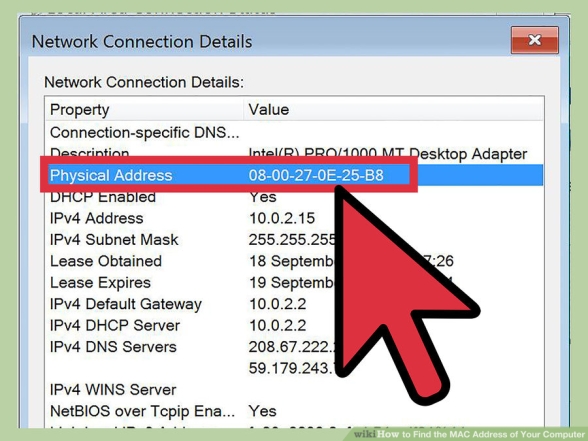
(How To Find The MAC)
Encryption Techniques-WPA 2
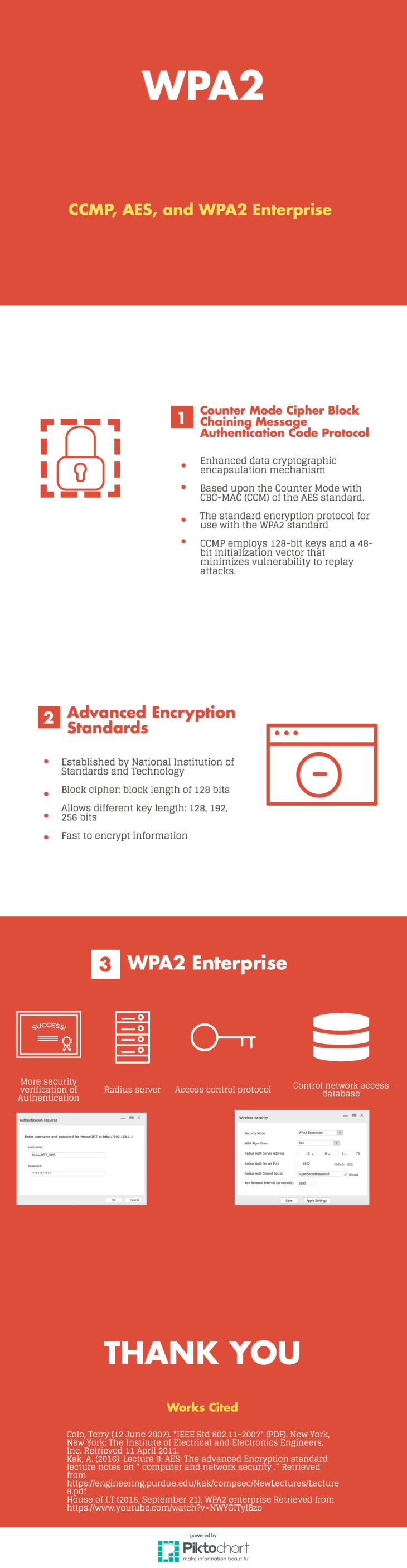
Personal Reflection: In this class, I understood the process of encryption and decryption. I recognized the close relationship between encryption and mathematics algorithm which makes computer science more appealing to me. I learned a particularly practical knowledge that websites with https in their URLs are secure. Therefore, when I am accessing websites without https in URL, I need to be more conscious.
Works Cited
“Introduction To Cryptography”. Infosectoday.com. N.p., 2016. Web. 7 Nov. 2016.
Google Privacy,. HTTPS And SSL Tutorial. 2011. Print.
“How To Find The MAC Address Of Your Computer”. wikiHow. N.p., 2016. Web. 7 Nov. 2016.

