Given a sorted array arr[] find the number of occurrences of a number.
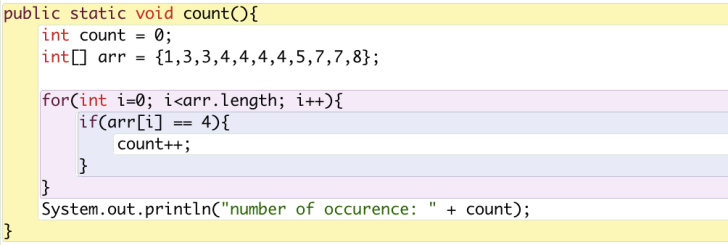
I loop all elements by using a for loop. Whenever an element equals to 4, count will add 1. Continue reading →

I loop all elements by using a for loop. Whenever an element equals to 4, count will add 1. Continue reading →
 

 

Operating System (OS)
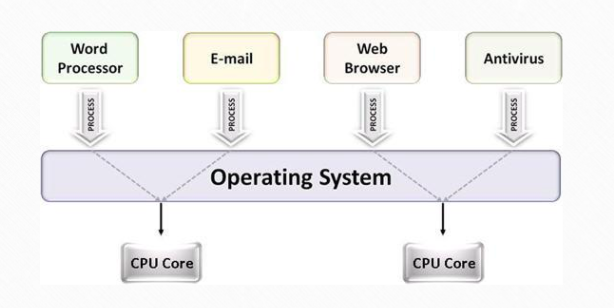
OS is the chief program that operates all hardwares and softwares. It has the control of process, files, sections of memory, and devices. It works as an intermediary, making sure that all hardwares and softwares are working correctly. Windows, Mac OS, Linux are examples of operating system. There are four essential managers working as a team to finish jobs and operating system is their boss.
To interact with the operating system, users reply on a user interface which gives us a visual understanding of what are trying to do when interacting with the system. For example, we click a file to give request, the managers will carry out the request by working together.
Graphical User Interfaces (GUIs) GUI allows users to interact with devices through graphical icons and visual indicators instead of text-based user interfaces, typed command labels or text navigation.
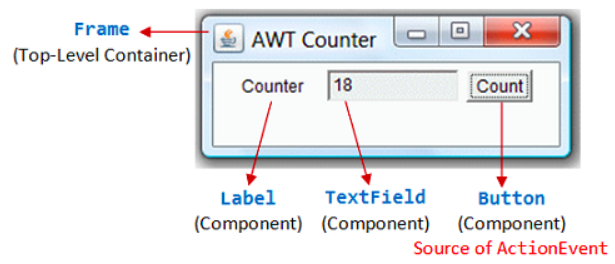 

Command Line Interfaces (CLIs) CLI allows users to interact with devices by issuing commands to the program in the form of successive lines of text (command lines). Terminal is an example.

Natural Language Interface (NLIs) NLI allows users to interact with devices via linguistic phenomena such as verbs, phrases and clauses. Siri is an example.
 

Menu Based Interface (MBIs) MBI allows user to interact with the devices via certain selections among several options. For example, when you open your computer, you may asked to select from guest account or administrator account.

Process manager decided how to allocate and deallocate jobs in CPU. Process manager keeps track of all process in CPU and serves as a traffic controller.
Multitasking refers to OS dividing the available processor time among the threads (jobs). For example, when you open your Web browser and then open Word at the same time, you are causing the operating system to do multitasking.

Device manager monitors every device, channel, and control unit. It has to choose the most efficient way to allocate all of the system devices that are connected to the computer. Peripheral device such as printers and external hard drives are examples.
Peripheral manager controls peripheral devices by sending them commands in their own computer language. The software routine that knows how to deal with each device is known as a driver. When a new peripheral is added, that device's driver is installed into the operating system. The operating system communicates with the computer's peripherals via the drivers for the devices.
 

File managers check every types of file on the system. For example, data files, program files, compilers, and installed application. It sets permissions so that certain users can only see certain files. For example, if you logged in as a guest in your computer, you cannot access to administrators' files because you are not allowed to do so by the file manger. Data manager coordinates the data transfer between disk and primary memory.
Memory manager is in charge of main memory. It scans every request from memory space keeps track of storage device and check if it is valid. It allows allocation of memory spaces that are not taken up already. And it will deallocate memory when a process no longer needs it or has been terminated. Specifically, memory manager allocates jobs to RAM (when there are multiple jobs, memory manager partition the space in RAM) and deallocate jobs when finished processing.
Network manager provides a way for users to share hardwares and softwares resources while control users' access to them and checks the extent to which their performance matches capacity plans and intra-enterprise service-level agreements Security manager prevents unauthorized access, for example via correct input of password.
 

 

Operation system is very important to the efficiency and consecution of a computer. It coordinate the interaction between softwares, computers, and devices, and allocate CPU's time to different programs. I learned that the mechanism of several operations that frequently appear in my computer. For example, when I connect a extra keyboard to my computer, a message saying that "installing device driver software" will appear. I learned that this means that the peripheral manager has take charge of the work of connecting peripheral keyboard to my computer using driver softwares (details see peripheral management above).
"Machine And Peripheral Management – Maisey, Liam." Sites.google.com. N. p., 2018. Web. 14 Jan. 2018.
Hi everyone. In this blog post we will take about what is application softwares, the three categories of their purposes, GUI and CLI, and concepts related to software management and release.
 

Application softwares allow users to perform non-computer tasks. They have three categories: general purpose,
General Purpose application softwares can be use for multiple purposes.
 

A word processor is a program for storing, manipulating, and formatting text entered from a keyboard and providing a printout. It enables users to fulfill various purposes: write papers, make posters, annotate documents, assert graphs and pictures, etc.
 

A spreadsheet enables calculation, storage of information, and automatically construct charts and graphs.
 

Database Management Systems (DBMS) manages databases and serves multiple users. It creates, stores, updates, modifies information in the database, and extracts information from the database after user called. MySQL and Oracle are DBMS.
 

Specific purpose application softwares are designed for one particular purpose. For example, a chess game application only allow users to play chess.
Email clients enables users to sent, receive, and manage emails. Outlook is an example of email client.
 

Web browsers retrieves, presents, and traverses information resources on the World Wide Web. Chrome, Safari, and FireFox are examples.
 

CADs assist users in the creation, modification, analysis, or optimization of a design. Automotive and architecture design are examples.
 

Graphic processing softwares enable users to manipulate visual images on a computer.
 

Bespoke purpose application software is customized for a specific user and purpose. For example, the processor applications of Audi's manufactures are customized for make Audi cars and automated invoicing system.
 

Toolbars
 

Menus that displays a list of commands
 

 

Dialogue Boxes that communicate information and wait for users' response of choice.
 

GUI components (WIMP: windows, icons, menus, and pointers)
 

Graphic user interface (GUI)is a type of user interface that allows users to interact with electronic devices through graphical icons and visual indicators.
Command-line interface (CLI) is a means that allow users to issue commands to a computer program in the form of successive lines of text (command lines).
 

Patches: update the application by fixing known bugs and vulnerabilities. For example, Windows's security update which is free and used to fixed potential flaws in the system to enhance security.
 

Upgrades: novel functionalities or characteristics and cumulative bug fixes (usually need to pay)
 

Updates: minor improvements and fixing known bugs (usually free)
 

Releases: final, working versions of software applications, new or upgraded applications (after alpha and beta testing)
 

Automatic updates: The system automatically checks for updates, download the update, and install the update.
Advantages:
- users: time saving and easy
- manufactures: no need to contact users
Disadvantages:
- users: miss updates if there is no Internet
- users: If updates bring a major change of system functions, users might not be informed about it.
Manual updates: The software manufacturer contacts every user about the new update and supplies the installation package to him to be installed.
Advantages:
- Users have more control what updates they want to install
- Users get to know if an update brings major changes to how the system works to make update decision
Disadvantages:
- Users might miss an update fixing security issues
- Users might not know how to install the update
- Users might harm system by wrongly installing update
- Users might lose medium containing the update
Encapsulation is the inclusion of both data and actions into a single component. The technique is to make fields private and provide public method to access the fields. Three benefits are: maintenance, flexibility, extensibility.
Inheritance ("is a") refers to the subclass inherit all the public properties of the superclass by using the keyword "extends". Four benefits are: reusability, extensibility, information hiding, and overriding.
Subclasses inherit same functionalities from superclass yet define their own unique behaviors. Two major advantages are: overriding and reusability.
Sign: Hollow Arrow
 

A1 uses and contains one instance of class B1 but B1 does not know the existence of A1. A1 has a B1.
 

A uses B's methods. A uses B.
 

An abstract class is a class that is not fully implemented. An abstract class cannot initiate objects and usually contains at least one abstract method.
An abstract super class defines the framework for subclass but provide subclasses opportunities to create their own unique functionalities under the predetermined framework.
Superclass:
public abstract void draw (Graphics g);
Subclass
public void draw( Graphics g )
{
int startY = getY( );
int startX = getX( );
g.setColor( Color.LIGHT_GRAY );
g.fillOval( startX - 37, startY + 8, 12, 12 ) ;
}
The program is about the race between hares and tortoises which are all inherited from abstract class Racer.
 

while ( input != 's' && input != 'S' )
{
Scanner in = new Scanner(System.in);
input = in.next().charAt(0);
switch(input){
case 'T':
case 't':
racerList.add(new Tortoise("Tortoise", START_LINE, yPos));
yPos += RACER_SPACE;
break;
case 'H':
case 'h':
racerList.add(new Hare("Hare", START_LINE, yPos));
yPos += RACER_SPACE;
break;
default:
JOptionPane.showMessageDialog( this, "Wrong, enter t or h please" );
}
It is a switch method. According to the user's input, the program will create a hare or a tortoise object. The creations of objects utilizes polymorphism. Tortoise and hare are both racer so they are stored together in the racerList array.
if ( raceIsOn )
{
for (Racer animal : racerList){
animal.move();
animal.draw(g);
}
}
else{
for (Racer animal : racerList){
animal.draw(g);
}
}
This section utilizes abstraction. move()and draw(g) are abstract method from abstract class Racer:
public abstract void move( );
public abstract void draw( Graphics g );
Hare and Tortoise have two different implementations of these two abstract methods but we can call these two different implementations in the same way. How amazing!
 

The most famous vide game among Chinese teenagers, The King Glory, employs polymorphism and abstraction. There are many different heroes with different skills, such as ZJ, YS, LB. However, ZJ, YS, LB all have the skill of beating the enemy but they beat in slightly different ways. ZJ, YS, LB are subclassed of the HERO superclass. HERO superclass is an abstract superclass which contains an abstract method called beat(). ZJ, YS, LB inherit the public methods and fields from HERO super class. They also inherit the abstract method beat() from HERO and create different implementation of beat(). Although they are different implementations, we can call all versions of beat() in the same way.
In this page, we will explore several different types of sorting algorithm, pseudocodes and Java programs of them, and their real life applications.
We choose an element first and compare each element in order with the chosen one. For example, searching for a word in a paper dictionary or searching a person in the phonebook apply sequential search as we find the targeted element by starting from the first one and end when we found it.
set POSITION to 0
set FOUND to false
loop while (POSITION < LENGTH and NOT FOUND)
if(numbers [position] quals searchitem) then
set FOUND to true
else
set POSITION to POSITION + 1
end loop
Binary search is about “compare and cut.” It is very important to know that we are looking for a target from an already sorted list. We compare the target value with the middle element on the list first and cut off the half that is far large or far small to the target. Then we compare the target with the new middle in the remained half of the list and repeat this “compare and cut” process until we found the target. Its application is on already sorted arrays.
 

Bubble sort is to repeat comparing two elements from the first to the last or from the last back to the first. Bubble sort is used in programming TV remote to sort channels on the basis of longer viewing time.
set firstUnsorted to 0
set SWAP to true
loop while (firstUnsorted < LENGTH - 1 and SWAP)
set SWAP to false
set INDEX to LENGTH - 1
while (INDEX > firstUnsorted)
if(DATA[INDEX] < DATA[INDEX-1])
swap DATA[INDEX] and data[INDEX-1]
set SWAP to true
set INDEX to INDEX-1
end loop
set firstUnsorted to firstUnsorted +1
end loop
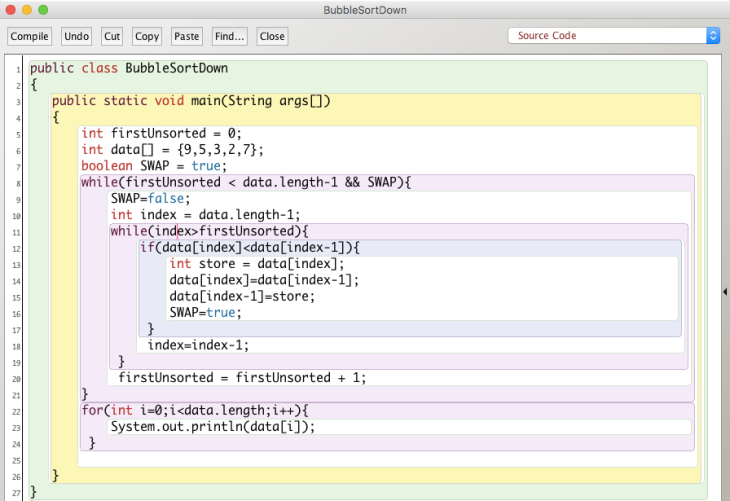 

The “Down” method check the order from the last element to the first. The system compare data[5] and data[4] first, if data[5] < data[4], it will swap their position by creating a temp to store data[5], equating data[5] to data[4], and equating data[4] to temp. Then, it will compare data[4] and data[3], data[3] and data[2]…until it reaches data[0] because the second while loop will stop when index>=firstUnsorted. Then firstUnsorted will increase for 1, and the comparison except the last element in the array will start over. SWAP is used as a flag here, making the program more efficient. If there is no swap in the whole second while loop, it means that all elements are sorted in the correct order, so there is no need to further check the order. The SWAP boolean will remain false and the first while loop will not be carry on further.
 

 

The “Up” Bubble sort starts comparing from the first element to the last one. Algorithm is the same as “Down” bubble sort.
set firstUnsorted to 0
loop while (firstUnsorted < LENGTH)
set indexOfSmallest = firstUnsorted
set INDEX = firstUnsorted + 1
loop while (INDEX <= LENGTH -1)
if(DATA[INDEX] < DATA[indexOFSmallest])
set indexOfSmallest to INDEX
end if
set INDEX to INDEX + 1
end loop
set temp = DATA[firstUnsorted]
set DATA[firstUnsorted] = DATA[indexOfSaallest]
set DATA[indexOfSmallest] = temp
set firstUnsorted to firstUnsorted + 1
end loop
 

We set the value of indexOfSmallest to be zero first and then loop the rest of the element to compare them will data[0]. Whenever an element is smaller than the value of current data[indexOfSmallest], it will replace this. Therefore, the program will find the smallest and put it to the data[0] position and start finding the second small value for data[1].
Selection sort is useful when certain program requires to output the numbers one by one from the largest to the smallest.
 

A standard that indicates the complexity of an algorithm.
O(n): one loop
O(n^2): one loop inside one loop
O(2n): two loops
By knowing different ways of sorting, I can choose the most efficient way to sort under different circumstances, for example, searching name in a phonebook (binary), sort TV channels based on viewing time (bubble), or output from the largest (selection), etc.
Kanungo, A. (2016). What are the uses of different sorting algorithms like bubble, selection, insertion, shell, merge, heap, quick, tree, radix, counting and bucket sort in real-life scenarios?. Quora. Retrieved 21 September 2017, from
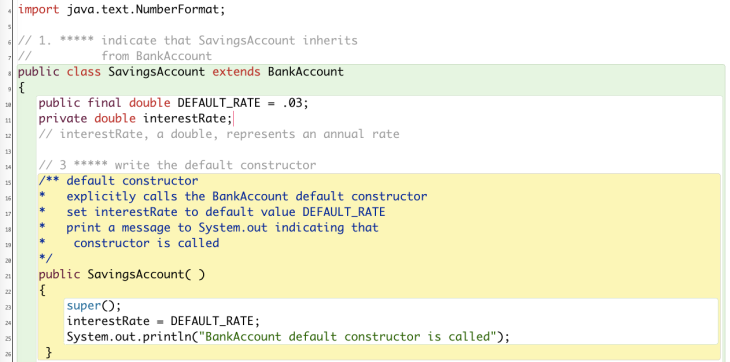
Line29 super() explicitly calls the superclass BankAccount default constructor. the private field interestRate is set to a fixed value 0.03.
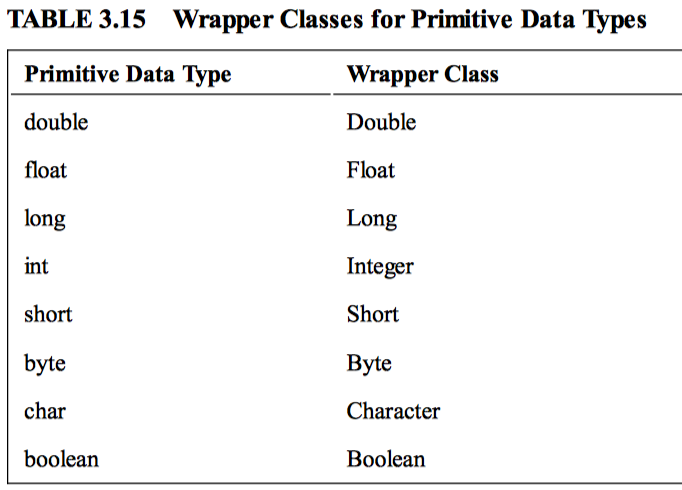
A wrapper class “wraps” the value of a primitive type, such as double or int, into an object.

The parseInt, parseDouble, and valueOf methods are static and are called using the Integer or Double class name and the dot notation. The parse methods convert a String to a primitive type, and the valueOf methods convert a String to a wrapper object.
Exercise 1

The first step is to read the file. Then I store the text from the file in a String called input. Then I loop the characters in input and output them line by line. Continue reading →